Your AI system is ready to launch. But is it truly safe? One overlooked vulnerability could lead to biased decisions, security breaches, or catastrophic failures. This comprehensive checklist ensures your AI deployment protects users, maintains trust, and delivers value without compromising safety.
Pre-Deployment Assessment
Risk Assessment and Categorization
Before any AI system goes live, classify its risk level:
- High Risk: Healthcare diagnostics, financial decisions, autonomous vehicles
- Medium Risk: Content moderation, customer service, recommendation systems
- Low Risk: Internal analytics, non-critical automation, research tools
✅ Complete risk matrix identifying:
- Potential failure modes
- Impact severity scores (1-10)
- Likelihood assessments
- Mitigation strategies for each risk
Stakeholder Identification
Map everyone affected by your AI system:
✅ Primary users and their technical capabilities ✅ Secondary stakeholders (customers, partners, regulators) ✅ Vulnerable populations potentially impacted ✅ Internal teams responsible for maintenance ✅ External auditors and oversight bodies
Baseline Performance Metrics
Establish clear success criteria:
✅ Accuracy thresholds (minimum 95% for critical applications) ✅ Response time requirements ✅ Resource consumption limits ✅ Error rate tolerances ✅ User satisfaction benchmarks
Technical Safety Measures
Model Testing and Validation
Rigorous testing prevents production failures:
✅ Unit testing for all model components ✅ Integration testing with existing systems ✅ Stress testing under 2x expected load ✅ Edge case testing with unusual inputs ✅ Adversarial testing against malicious inputs ✅ A/B testing comparing to current solutions
Security Hardening Steps
Protect your AI from attacks:
✅ Input validation preventing injection attacks ✅ API rate limiting and authentication ✅ Model encryption at rest and in transit ✅ Access control with principle of least privilege ✅ Regular security vulnerability scans ✅ Penetration testing by external experts
Monitoring Infrastructure Setup
Real-time visibility ensures quick response:
✅ Performance dashboards tracking key metrics ✅ Anomaly detection for unusual patterns ✅ Log aggregation and analysis tools ✅ Alert systems for critical issues ✅ Resource usage monitoring ✅ User behavior analytics
Ethical and Bias Evaluation
Fairness Testing Procedures
Ensure equitable treatment across demographics:
✅ Dataset diversity analysis ✅ Output distribution testing by protected classes ✅ Disparate impact assessments ✅ Individual fairness evaluations ✅ Counterfactual fairness testing ✅ Third-party fairness audits
Bias Detection Methods
Systematic bias identification:
✅ Statistical parity measurements ✅ Demographic parity testing ✅ Equal opportunity analysis ✅ Calibration checks across groups ✅ Feature importance analysis for bias indicators ✅ Human-in-the-loop bias reviews
Impact Assessment Protocols
Understand broader implications:
✅ Privacy impact assessments ✅ Social impact evaluations ✅ Environmental footprint calculations ✅ Economic displacement analysis ✅ Psychological effect studies ✅ Long-term consequence modeling
Compliance and Documentation
Regulatory Requirements
Navigate the legal landscape:
✅ GDPR compliance for EU operations ✅ CCPA adherence for California users ✅ Industry-specific regulations (HIPAA, SOX, etc.) ✅ Local AI governance laws ✅ Export control compliance ✅ Age-appropriate design standards
Documentation Standards
Comprehensive records enable accountability:
✅ Technical architecture documentation ✅ Training data provenance records ✅ Model decision explanations ✅ Testing methodology descriptions ✅ Known limitations disclosure ✅ User guide creation
Audit Trail Preparation
Enable thorough reviews:
✅ Version control for all models ✅ Change log maintenance ✅ Decision logging for critical outputs ✅ Access logs for sensitive operations ✅ Compliance checkpoint records ✅ Third-party audit preparations
Operational Readiness
Team Training Requirements
Prepare your human operators:
✅ Technical operation training ✅ Ethics and bias awareness sessions ✅ Incident response drills ✅ Monitoring tool proficiency ✅ Customer communication skills ✅ Regulatory compliance understanding
Incident Response Planning
Prepare for the unexpected:
✅ Incident classification system ✅ Response team roles and responsibilities ✅ Communication trees and protocols ✅ Remediation playbooks ✅ Post-incident review processes ✅ Customer notification procedures
Rollback Procedures
Enable quick reversions:
✅ Rollback triggers defined ✅ Previous version availability ✅ Data migration strategies ✅ User communication templates ✅ Testing protocols for rollbacks ✅ Decision criteria documentation
Post-Deployment Monitoring
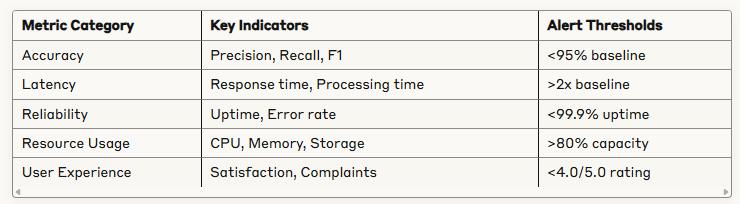
Performance Tracking Metrics
Monitor what matters:
Continuous Testing Protocols
Never stop validating:
✅ Daily automated test suites ✅ Weekly performance reviews ✅ Monthly bias assessments ✅ Quarterly security audits ✅ Annual comprehensive evaluations ✅ Continuous user feedback collection
User Feedback Mechanisms
Listen to your users:
✅ In-app feedback buttons ✅ Regular user surveys ✅ Focus group sessions ✅ Support ticket analysis ✅ Social media monitoring ✅ User behavior analytics
Emergency Response Planning
Kill Switch Implementation
Enable immediate shutdown:
✅ Manual override controls ✅ Automated trigger conditions ✅ Partial shutdown capabilities ✅ Graceful degradation options ✅ Data preservation protocols ✅ Recovery procedures
Escalation Procedures
Clear chain of command:
✅ Level 1: Operations team (0-5 minutes) ✅ Level 2: Engineering leads (5-15 minutes) ✅ Level 3: Executive team (15-30 minutes) ✅ Level 4: Board notification (30+ minutes) ✅ External stakeholder communication ✅ Regulatory body notification
Communication Protocols
Keep everyone informed:
✅ Internal status pages ✅ Customer notification systems ✅ Media response templates ✅ Regulatory reporting procedures ✅ Partner communication channels ✅ Public statement preparations
Implementation Guidelines
Phase Your Deployment
Start small and scale safely:
- Pilot Phase (5% of users)
- Limited rollout
- Intensive monitoring
- Quick iteration capability
- Beta Phase (25% of users)
- Broader testing
- Performance validation
- User feedback integration
- General Availability (100% of users)
- Full deployment
- Continuous monitoring
- Regular updates
Key Success Factors
- Executive Sponsorship: Ensure leadership commitment to safety
- Cross-functional Teams: Include diverse perspectives
- Regular Reviews: Schedule monthly safety assessments
- User-Centric Focus: Prioritize user safety and experience
- Continuous Improvement: Update checklist based on learnings
Checklist Summary
Safe AI deployment requires systematic preparation across multiple dimensions. This checklist provides a foundation, but remember:
- Customize for your specific use case
- Update regularly as regulations evolve
- Test thoroughly before each deployment
- Document everything for accountability
- Prioritize user safety above all else
The difference between successful AI deployment and catastrophic failure often lies in the details. Use this checklist as your safety net, ensuring every deployment protects users while delivering transformative value.
Unlock your AI Edge — Free Content Creation Checklist
Get the exact AI-powered process to 10X your content output — blogs, emails, videos, and more — in half the time.
No fluff. No spam. Just real results with AI.